We deliver risk-driven, multi-level infrastructure, systems, data protection, and agile cyber integration to support large and small IT ecosystems. Our cost-effective, scalable solutions are tailored to your organizational needs that will align to your desired security outcomes.
- Our Cybersecurity Apprenticeship Program has prepared the next generation of professionals via hands-on curricula (e.g., Zero Trust, GRC, Cyber Engineering, SOC) and certifications (e.g., CAP, CySA+, CCSP, CISSP). The Cybersecurity Apprenticeship Program empowers apprentices to become experts in Government standards and industry best practices.
- Our Zero Trust Advisors guide agencies like NOAA, NTIA, and DoDEA in strategizing and implementing Zero Trust Architecture frameworks to ensure resilience and compliance. We align organizations to Zero Trust standards, increase capabilities, and reduce costs. At NOAA, we implemented hyper converged infrastructure resulting in $375k in savings in licensing costs alone per year, and storage optimizations at NTIA saved $1M per year. At DoDEA, IBSS modernized their log management, saving them $2.5M per year. For more information, visit our Zero Trust page.
- Since 2014, IBSS has provided full-spectrum cybersecurity services to support DoDEA’s security operations, engineering, and analytics. Our work led to an 86% threat surface reduction and 96% client approval.
- IBSS is an authorized C3PAO providing independent, objective, and DoD-aligned CMMC Level 2 assessments for DoD contractors ready to certify.
Zero Trust Strategy & Engineering Services
IBSS is at the forefront of federal Zero Trust strategy, project management, and engineering service delivery. We partner with federal CIOs, CTOs, and CISOs to develop strategies and roadmaps empowering agencies to achieve their desired Zero Trust outcomes on time and under budget. Our experienced team of project managers and engineers have performed the Zero Trust assessments, developed the strategies and roadmaps, and provided analysis of alternatives, pilots, implementations, and integrations required to make Zero Trust successful across the federal government, both civilian and defense. Read more about our Zero Trust Architecture.
- Applications & Workloads
- Automation & Orchestration
- Data
- Devices
- Governance
- Identity/User
- Network & Environment
- Visibility & Analytics
Identity, Credential, & Access
Management (ICAM)
IBSS’ ICAM cybersecurity services provide increased security within an organization and diminished identity theft incidents, fewer data breach cases, and higher levels of trust. IBSS establishes how organizations manage, consolidate, and store user identities; issue, revoke, and validate credentials; and securely manage application sessions for individuals to provide trustworthy and interoperable access to resources. We offer expert resources in Identity, Credential, and Access Management (ICAM) solutions that fully comply with OMB, HSPD-12, CDM, and Federal Public Key Infrastructure Policy Authority Audit requirements. IBSS’ cybersecurity team deploy scalable and highly available systems using industry standard protocols (SAML, OpenIDC, and OAuth2) to agencies such as DoDEA, DOC, NTIA, and NOAA.
- Access Management/Single Sign-on (SSO)
- Identity Governance and Administration
- Privileged Access Management (PAM)
- Zero Trust Security
Governance, Risk Management,
& Compliance (GRC)
IBSS is your trusted advisor for developing and implementing cybersecurity governance strategies, cost-effectively managing risks to achieve mission and business objectives, and navigating complex legal and regulatory compliance requirements. The IBSS suite of GRC services focus on resilience and measures to protect the confidentiality, integrity, and availability of sensitive organizational data and organizational systems that display, process, store, and transmit the data.
We provide expert support to promote compliance with Defense Federal Acquisition Regulation Supplement (DFARS), NIST SP 800-171, Cybersecurity Maturity Model Certification (CMMC), Federal Information Security Modernization Act (FISMA), Federal Risk and Authorization Management Program (FedRAMP), and Privacy requirements.
Governance
- Framework Identification and Implementation
- Integrating Security into the SDLC
- Metrics Development
- Strategy and Planning
Risk Management
- Audits and Assessments
- Risk Assessment
- Map Cybersecurity Risks to Business Risks
- Threat Analysis
- Vulnerability Analysis
Compliance
- Gap Analysis Tailored to Your Compliance Needs
- Federal Requirements: DHS BODs, Executive Orders, FedRAMP, FISMA, GAO, OMB
- Contractor Requirements: CMMC, DFARS, FAR
- Policy Guidance and Development
- Standards: CIS Benchmarks, DISA STIGS, FIPS, NIST CSF, NIST Special Publications
Endpoint Detection & Response (EDR)
IBSS designs, implements, and manages next-gen Endpoint Detection and Response (EDR) deployments that protect your endpoints from compromise. We have experience leveraging AI/ML capabilities with EDR that use heuristics and signatures to prevent potential compromise. Skilled with on-premise and cloud-based EDR solutions, IBSS provides customers a clear advantage in maximizing EDR capabilities while minimizing impact to normal operations.
- AI/ML-based Threat Detection
- Enhanced Security Analysis and Investigation
- Integration with Other Security Tools
- Response Automation
- Threat Intelligence Integration
Security Operations
IBSS provides 24×7×365 continuous monitoring of your environment for internal and external threats. We develop specialized detection rules based on the MITRE ATT&CK and Cyber Kill Chain frameworks and leverage next-gen technologies to discover and disrupt attacker tactics, techniques, and procedures to strengthen your organization’s security posture. We understand the impact cyber attacks have on Federal organizations and have unparalleled skills in quickly identifying, containing, and remediating cyber incidents. Whether for small agencies or entire departments, IBSS provides experienced and capable personnel ready for your organization’s needs.
- 24x7x365 Cybersecurity Monitoring
- Enterprise Incident Management
- Security Information and Event Management (SIEM)
- Security Orchestration, Automation and Response (SOAR)
- Threat Hunting
- Vulnerability and Threat Management
Check Out Our NIST SP 800-171 Solution
Learn More About IBSS' Commercial Cybersecurity Spin-Off Company, Total Assure
Related Insights
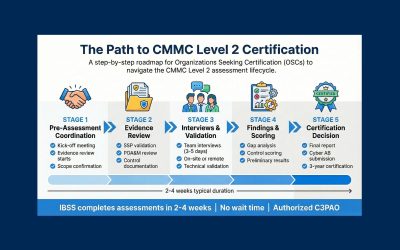
Understanding the C3PAO Assessment Process for CMMC Level 2
Looking for the best C3PAOs for short project timelines? IBSS is a Cyber AB-authorized C3PAO with open availability now for CMMC Level 2 assessments. Request your slot today.
CMMC Certification in Maryland: What You Need to Know
IBSS is an authorized C3PAO conducting official CMMC Level 2 assessments for Maryland defense contractors.
The Road to CMMC Level 2: Timeline, Requirements, and What to Expect
CMMC Level 2 is a requirement for many DoD contracts. Learn what to expect on your path to certification and how IBSS can help you get there with confidence.