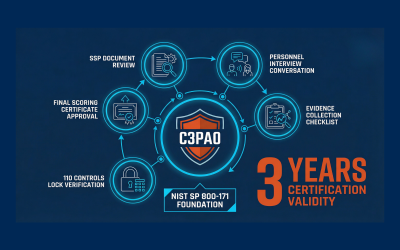
Not sure what a C3PAO is or why it’s critical to your CMMC success? Learn why you’ll need one to achieve Level 2 certification as a DoD contractor.
CMMC 2.0 Explained: What DoD Contractors Need to Know in 2026
CMMC 2.0 is here…are you ready?
Total Assure, an IBSS Company, Partners with Breacher.ai to Combat the Rise of AI-Powered Deepfake Threats
Together, Total Assure and Breacher.ai are providing businesses with actionable defenses to counter AI-driven threats that traditional security measures fail to address.
Mastering NIST SP 800-171 Compliance: Insights from IBSS’ LinkedIn Live Series
At IBSS, we bring over 20 years of DoD cybersecurity experience to help organizations understand and achieve NIST SP 800-171 compliance.
Cybersecurity Awareness Month: Recognizing and Reporting Phishing
Despite the best user training and rigorous best practices, users still make mistakes. Fortunately, several established and emerging endpoint and network security technologies can help security teams combat phishing.
Cybersecurity Awareness Month: Cyber Hygiene
IBSS emphasizes the critical role of cyber hygiene in protecting individuals and organizations online.
Cybersecurity Awareness Month: Cyber Hygiene and Updating Software
IBSS highlights the critical importance of cyber hygiene and software updates for online safety. It outlines essential practices like strong passwords, role-based access, and regular backups, while also warning against common mistakes and fake updates.
October Is Cybersecurity Awareness Month: Multi-Factor Authentication
IBSS focuses on essential techniques to stay safe online, highlighting the power of Multi-Factor Authentication (MFA), which thwarts over 99.9% of account takeovers.
Cybersecurity Awareness Month: Creating a Secure Digital Future
By focusing on preventative measures and ongoing vigilance, we can mitigate risks and build a safer, more secure digital future for everyone. Let’s use this month to spread the message of cybersecurity awareness, take action, and foster partnerships that create a resilient and secure cyber environment.