In Search of the Perfect Bite: Hawaiian Kanpachi in Rice Paper
Hawaiian Kanpachi is prized for its clean flavor and firm texture. In this dish, it’s crisped to perfection and paired with bold, ocean-inspired accompaniments.
Cybersecurity on the Go: Best Practices for Remote and Hybrid Workers
IBSS’ customized cybersecurity strategies ensure your remote and hybrid workforce stays secure without sacrificing productivity.
Olympic College Presentation: The Merroir of Ocean-Farmed Seafood
Understanding Merroir concepts gave students a deeper appreciation for the seafood’s origins and qualities.
Bonney Lake High School Culinary Team Wins 2025 ProStart Invitational
The Bonney Lake High School culinary team presented their event-winning Miso Glazed Sablefish with an apple fennel slaw and pickled carrot.
In Search of the Perfect Bite: Irish Seafood Chowder
Irish Seafood Chowder features fish, potatoes, onions, celery, leeks, and cream which defines it’s key characteristic – lightness.
Are You Prepared for a Tornado?
Having a reliable source of weather updates is critical. A NOAA Weather Radio can provide real-time alerts, even if power or cell service is lost.
In Search of the Perfect Bite – Geoduck Fritters and Black Bean Clams
Leaving geoducks in their “home” is important because if you are not going to eat a geoduck, please let it live in peace for the rest of its 140+ years.
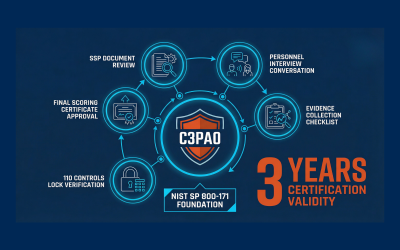
What Is a C3PAO and Why Does It Matter for Your CMMC Certification?
Not sure what a C3PAO is or why it’s critical to your CMMC success? Learn why you’ll need one to achieve Level 2 certification as a DoD contractor.
CMMC 2.0 Explained: What DoD Contractors Need to Know in 2026
CMMC 2.0 is here…are you ready?