Looking for the best C3PAOs for short project timelines? IBSS is a Cyber AB-authorized C3PAO with open availability now for CMMC Level 2 assessments. Request your slot today.
CMMC Certification in Maryland: What You Need to Know
IBSS is an authorized C3PAO conducting official CMMC Level 2 assessments for Maryland defense contractors.
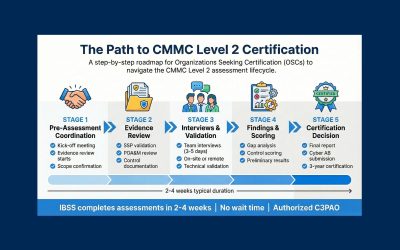
The Road to CMMC Level 2: Timeline, Requirements, and What to Expect
CMMC Level 2 is a requirement for many DoD contracts. Learn what to expect on your path to certification and how IBSS can help you get there with confidence.
Beware of Misleading C3PAO Claims
Confused about C3PAOs and CMMC certification? Discover why C3PAOs only certify, not prepare, and how misleading claims can put your DoD contracts at risk.
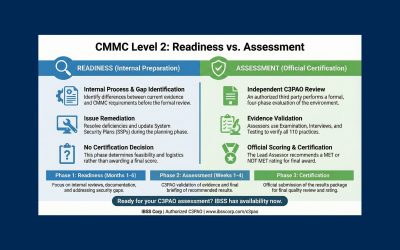
Understanding the Difference Between CMMC Readiness and C3PAO Assessment
Confused about the difference between CMMC readiness and a C3PAO assessment? You’re not alone.
Frequently Asked Questions About C3PAOs and Certification
What actually happens during a CMMC assessment? This FAQ explains what to expect and who C3PAOs really are.
CMMC: A Business Requirement You Can’t Ignore
CMMC is now a business requirement for defense contractors. Learn how certification impacts eligibility, competitiveness, and long-term growth.
What to Expect When Working With a C3PAO
From initial inquiry to official reporting, see how IBSS’ four-phase CMMC assessment process delivers a clear, professional certification experience.
Your Choice of C3PAO Matters More Than You Think
Your C3PAO choice can impact timelines, clarity, and outcomes. Discover what to look for in a CMMC assessor and why it matters.