Preparing for CMMC Level 2 in 2026? Limited C3PAO availability makes early assessment planning critical for defense contractors handling CUI.
CMMC Certification in Virginia: How IBSS Supports Local Defense Contractors
IBSS is an authorized C3PAO conducting official CMMC Level 2 assessments for Virginia defense contractors.
Fast and Accurate CMMC Certification Services for Defense Contractors
Need CMMC C3PAO certification services? IBSS delivers fast, reliable Level 2 assessments with accredited assessors experienced in DoD requirements and NIST SP 800-171.
IBSS Achieves Official Authorization as a CMMC Level 2 C3PAO
IBSS has been approved by The Cyber AB as a CMMC Level 2 C3PAO and is currently accepting new assessment appointments. Connect with our experts to begin your certification journey.
What Sets IBSS Apart as a C3PAO: Our Approach to Assessment and Support
Discover what sets IBSS apart as an Authorized C3PAO.
The Future of CMMC: What to Expect in 2026 and Beyond
IBSS, an Authorized CMMC Level 2 C3PAO, breaks down what contractors can expect from CMMC in 2026 and beyond. Explore key trends and schedule your assessment.
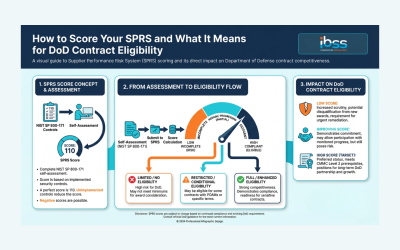
Understanding Your SPRS Score: What It Means for DoD Contract Eligibility and CMMC Level 2
A quick guide to understanding, calculating, and improving your SPRS score to stay eligible for DoD contracts.
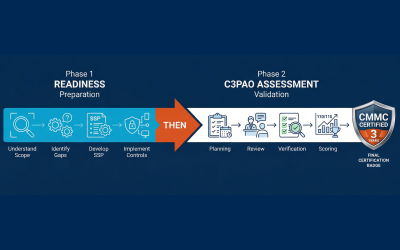
How to Prepare for a Successful C3PAO Assessment
From defining your scope to organizing your documentation and training your team, here are the must-do steps to obtain your CMMC Level 2 certification with confidence.
What Is NIST SP 800-171? A Simple Guide for DoD Contractors
New to NIST SP 800-171? This straightforward guide explains what it is, why it matters for DoD contractors, and how IBSS helps you meet compliance requirements with confidence.