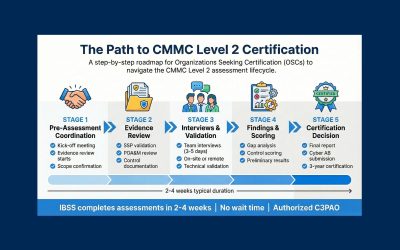
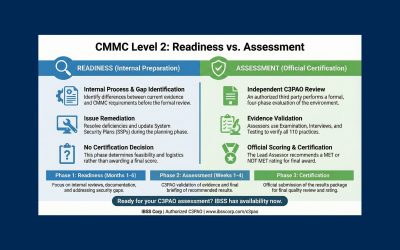
If you’re new to Zero Trust, here are practical tips to help you start strong, without having to overhaul everything at once.
1. Start with Visibility
You can’t protect what you can’t see. This will give you an overview of your current access environment and risk exposure, and help prioritize where to implement controls first. Start by identifying:
- Who is accessing your network (users, roles).
- What they’re accessing (apps, data, devices).
- When and how (location, time of day, device posture).
Tip: Use existing tools like log aggregators or identity providers to map your current access patterns.
2. Implement Strong Identity Controls
Zero Trust starts with identity. Make sure every user and device is authenticated and authorized before granting access.
Begin with:
- Multi-factor authentication (MFA).
- Role-based access control (RBAC).
- Conditional access policies (e.g., only allow access from approved devices or geographies).
Tip: MFA is often the easiest Zero Trust measure to implement and it significantly reduces your risk.
3. Segment Your Network
Don’t let attackers move freely if they break in. Zero Trust promotes microsegmentation, which means dividing your network into smaller zones so access is limited to what’s truly needed. For example, your team might start by isolating critical assets (like servers or sensitive data stores) from the broader network.
4. Strong Identity Control
Users should have just enough access to do their job and nothing more. This minimizes the damage if credentials are compromised. Zero Trust is about intentional access, not convenience-based permissions.
Audit user roles regularly. Look out for:
- Admin privileges that aren’t needed.
- Shared accounts with broad access.
- Forgotten service accounts.
5. Continuously Monitor Everything
Zero Trust requires continuous verification. Even with tight access controls, monitoring helps you catch unusual behavior that slips through, such as an account accessing data at odd hours or from an unexpected country.
Use tools like:
- Endpoint Detection & Response (EDR).
- Security Information and Event Management (SIEM).
- User and Entity Behavior Analytics (UEBA).
6. Don’t Go it Alone
Zero Trust isn’t one-size-fits-all. At IBSS, we help organizations build Zero Trust strategies that align with their business, compliance, and budget needs. We’ve helped agencies like NOAA, NTIA, and DoDEA successfully adopt Zero Trust, saving millions in the process while meeting compliance standards. Whether you’re starting from scratch or building on existing frameworks like NIST SP 800-171 or CMMC, our team is here to support your journey.
Your Zero Trust cybersecurity practice involves your entire team. Start small, prioritize what matters most, and build from there. Need help getting started? Contact IBSS today for a consultation and let’s build a more secure, modern environment together.
About IBSS
Since 1992, IBSS has provided transformational consulting services to the Federal defense, civilian, and commercial sectors. Our services include cybersecurity and enterprise information technology, environmental science and engineering (including oceans, coasts, climate, weather, and satellite), and professional management services.
Our approach is to serve our employees by investing in their growth and development. As a result, our employees bring greater capabilities and provide an exceptional level of service to our clients. In addition to creating career development opportunities for our employees, IBSS is passionate about giving back to the community. We strive to leave something better behind for the next generation.
We measure our success by the positive impact we have on our employees, clients, partners, and the communities we serve. Our tagline, Powered by Excellence, is a recognition of the employees that make up IBSS and ensures we deliver results with quality, applying industry best practices and certifications. Read more About Us.
Keywords: Zero Trust, Cybersecurity, Endpoint Detection & Response, Cyber Security