Our Zero Trust Advisors guide agencies like NOAA, NTIA, and DoDEA in strategizing and implementing Zero Trust Architecture frameworks to ensure resilience and compliance. We align organizations to Zero Trust standards, increase capabilities, and reduce costs. At NOAA, we implemented hyper converged infrastructure resulting in $375k in savings in licensing costs alone per year, and storage optimizations at NTIA saved $1M per year. At DoDEA, IBSS modernized their log management, saving them $2.5M per year.
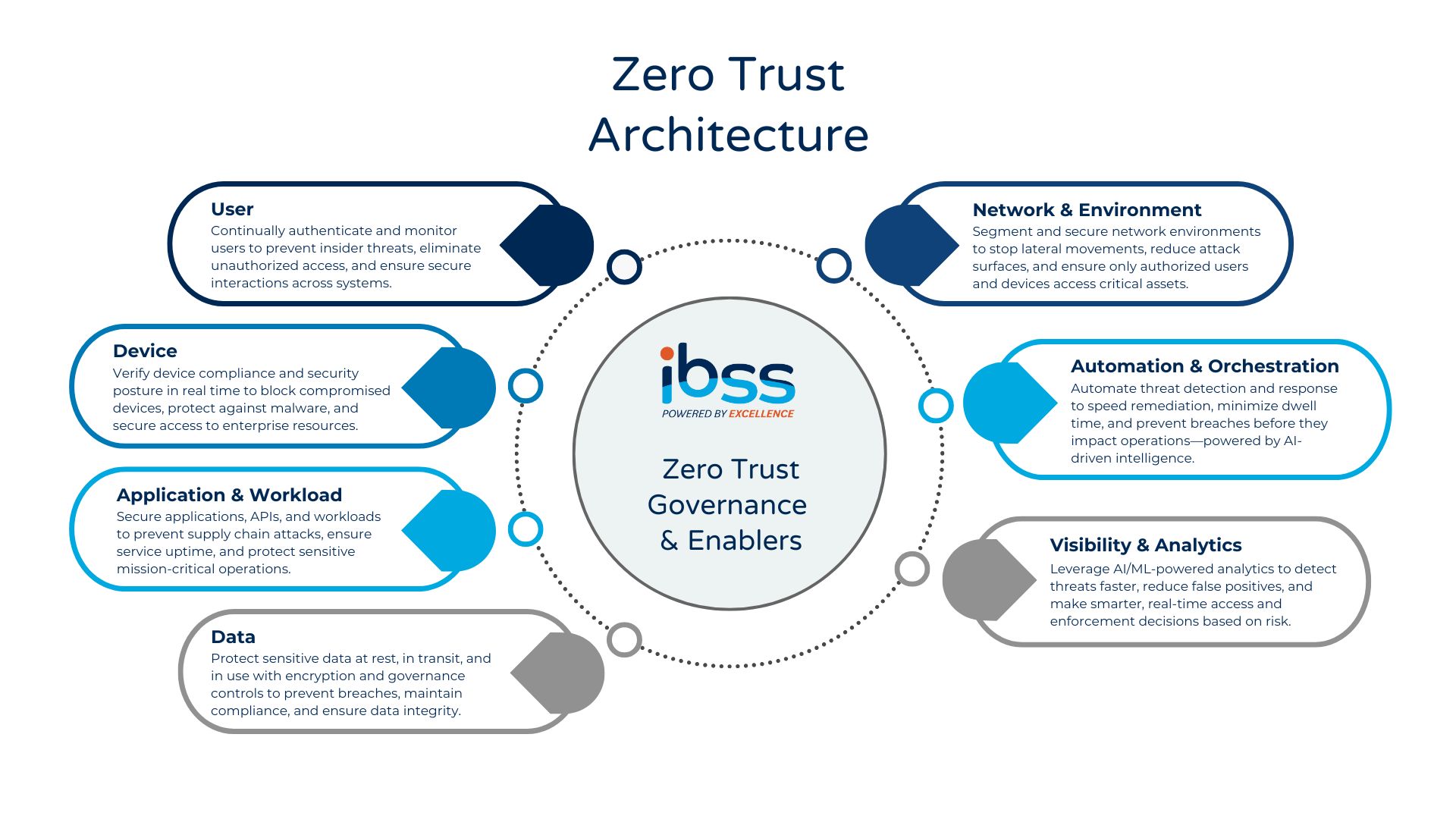
What Is Zero Trust?
As a government agency, safeguarding sensitive information and earning your constituents’ trust is essential. But with cyber threats becoming increasingly advanced, relying solely on traditional perimeter defenses isn’t enough. Zero Trust Architecture (ZTA) provides a stronger, more comprehensive approach by verifying every user and device before granting access to your network, data, and resources.
At IBSS, we specialize in delivering tailored Zero Trust solutions to government agencies like yours. Our team of experts has a deep understanding of the unique security challenges faced by federal, state, and local governments. We have experience providing ZTA guidance for both small and large user populations. At the National Telecommunications and Information Administration, we ensure observability into enterprise operations and apply ZTA principles to comport with CISA TIC 3.0 Reference Architecture for 500 users. At the Department of Defense Education Activity (DoDEA), we teamed with Microsoft and Google to migrate DoDEA from an on-premise datacenter to the cloud, ensuring compliance with the DOD ZTA requirements and DOD 7 ZTA pillars. We’ll work closely with you to assess your current security posture, identify vulnerabilities, and develop a customized plan to implement a comprehensive Zero Trust Architecture. From network segmentation and access control to identity management and continuous monitoring, we’ll help you build a robust defense that meets the evolving needs of your agency.
Benefits to IBSS’ Approach
Our Zero Trust services are designed to be flexible and scalable, allowing us to accommodate the diverse security requirements of government agencies. Whether you’re looking to enhance your existing security infrastructure or implement a new zero-trust-based network, IBSS is here to support you every step of the way. Our team will collaborate with your stakeholders to ensure that our solutions align with your agency’s mission and goals, while also meeting the stringent security standards set by government regulations. We guide your organization throughout the design and planning stages, using zero trust requirements to identify salient capabilities for your organization. As needed, we align existing technologies and processes to meet these capabilities. We facilitate market research and assess vendors agnostically to ensure proper fit with customer organizations.
Requirements
In recent years, the federal government has made clear its commitment to implementing Zero Trust Architecture across all agencies. The White House Executive Order 14028 on Improving the Nation’s Cybersecurity emphasizes the importance of zero-trust-based network architectures in protecting sensitive information and preventing cyber threats. Additionally, the Office of Management and Budget (OMB) Memorandum M-22-09 requires federal agencies to implement Zero Trust Architecture as part of their overall cybersecurity strategy, to include 91 zero trust activities required for DoD agencies by the end of FY 2027. At IBSS, we’re well-versed in these requirements and are dedicated to helping government agencies like yours deploy NIST SP 800-207 compliant architectures. Our expertise will ensure that your agency’s Zero Trust implementation aligns with the latest guidance from CISA and other government stakeholders.
IBSS Certifications
- ISO 9001:2015 Certified Quality Management System (QMS)
- ISO/IEC 20000-1:2018 Certified Information Technology Service Management (ITSM)
- ISO/IEC 27001-2022 Certified Information Security Management System (ISMS)
- Capability Maturity Model Integration (CMMI) – SVC Level 3 and DEV Level 3
