Overview
The Department of Defense (DoD) Department of Defense Education Activity (DoDEA) Information Technology (IT) Division provides reliable and innovative technology solutions to support 80,000 military-connected users, consisting of approximately 60,000 students and 20,000 educators and administrators across multiple learning environments. These global environments cover 161 accredited schools in 9 districts located in 11 foreign countries, 7 states, Guam, and Puerto Rico. As part of the DoD and .edu domains, DoDEA has unique security, architecture, and engineering needs, as well as designing, implementing, and operating its own global network, to include direct internet access circuits and Multiprotocol Label Switching (MPLS) network. Infrastructure and systems must be compliant with DoD security requirements while accounting for DoDEA’s unique challenge of operating in and meeting both DoD and Commercial security requirements wherever possible.
DoDEA is required to implement Zero Trust Architecture (ZTA) by 2027, accelerate movement to secure cloud services (including Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS)), centralize and streamline access to cybersecurity data to drive analytics for identifying and managing cybersecurity risks, and invest in both technology and personnel to match these modernization goals by 2027. This includes periodic check-ins with the DoD Chief Information Officer (CIO), the Pentagon, and other security agencies such as the Defense Information Systems Agency (DISA).
Customer’s Challenges
- Instead of modern endpoint detection and response (EDR) focused solutions, DoDEA depended on a legacy anti-virus (AV) system that utilized a signature-based and knowledge-based approach, which did not offer adequate zero-day threat protection and necessitated weekly full AV scans that significantly impacted network performance.
- DoDEA used Trellix, a third party tool, which required the installation of an agent on all devices in the environment to secure them with the point products such as AV, leading to potential security gaps, increased likelihood of human error, and introduced an additional step in the security process.
- Zero Trust (ZT) concepts and implementation strategies were new to the DoD and DoDEA, which led to a slow adoption approach with some staff resistance due to inexperience and uncertainty. In addition, configuration guidelines had not been released by the DoD to formalize MDE configuration expectations, making it challenging to develop realistic roadmaps to adopt ZT requirements.
- DoD has not been formally approving the migration from legacy endpoint protection platforms to more modern EDR-based endpoint security platforms without an exception to policy.
IBSS’ Assessment
Initially, IBSS’ ZT Endpoint Security Engineers performed an assessment that identified the following risks and recommended potential mitigation strategies:
Challenge: There were no standardized instructions on how the DoD expected Microsoft Defender for Endpoint (MDE) to be configured within the DoDEA environment.
-
- Approach: Our engineers recommended working with the Microsoft (MS) subject matter experts (SMEs), in collaboration with the Defense Information Systems Agency (DISA) and the Joint Force Headquarters – Department of Defense Information Network (JFHQ–DODIN), to build tailored requirements that fit DoDEA’s unique environment.
Challenge: A threat roll-up solution had not been finalized.
-
- Approach: IBSS consulted with DISA on additional challenges regarding the status of the to-be system: Security Event Data Repository (SEDR).
Challenge: There was a chance that implementing a hybrid-cloud environment could impact the success and stability of configuration changes. Similarly, multiple MDM technologies on premise and in the cloud could cause policy conflicts, leading to further instability in the DoDEA environment.
-
- Approach: Our team worked with DoDEA to migrate to Intune (Cloud MDM) and began shifting off of MS Endpoint Configuration Manager(MECM) in favor of Entra ID, DoDEA’s current on-premise MDM solution.
As part of the assessment, IBSS’ team used existing knowledge and understanding of the DoDEA environment and pain points to develop and propose an architecture and deployment strategy. Below is the high-level proposed strategy for Microsoft Defender for Endpoint architecture and deployment.
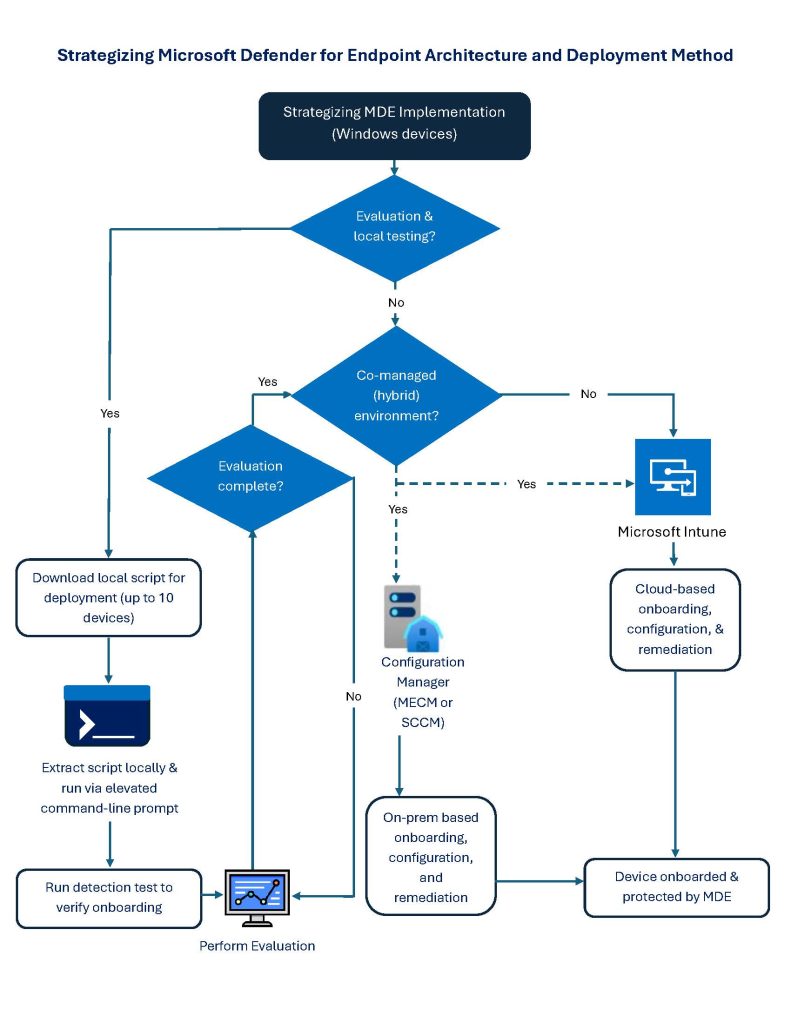
Benefits of Working with IBSS
Throughout this effort, IBSS focused on identifying opportunities to reduce the on-premise footprint by eliminating hardware and license requirements associated with the physical datacenter and modifying requirements for operating system (OS) and Structured Query Language (SQL) licenses (Trellix). For example, we collaborated with SMEs and SIEM Engineers to minimize irrelevant log entries and reduce data ingestion requirements. This allowed analysts to focus on critical threats and save DoDEA an estimated $22k a month through a reduction in cost from $4.26/GB to $1.50/GB. In addition, working with IBSS has resulted in the following benefits for DoDEA:
- DoDEA operates primarily with MS products; as a result, MS Defender Antivirus (AV) was built into the OS and the Endpoint Detection and Response (EDR) will communicate and function properly as long as an internet connection is present. This eliminated reliance on virtual private network (VPN) connections or the presence of a third party agent like Trellix for proper communication with devices in the environment.
- Microsoft Defender for Endpoint (MDE) uses Artificial Intelligence and Machine Learning (AI/ML) behavioral-based protection with signature-based supplementation to catch known and unknown (zero day) threats. This technology is considered superior, as automation capabilities catch malicious activities that would otherwise be undetected on legacy endpoint protection platforms, and free up IT resources and personnel to focus on more critical tasks and/or threats. Transitioning to MDE, which uses the performance benefits of cloud technology to remain continuously up-to-date and analyze environments, the IT Division gained the capability of interacting with data and analyzing behavior for threats instantly without impacting performance for users.
- Endpoint Engineering and Operations play a pivotal role for DoDEA by ensuring that every device is properly configured and managed to align with the ZT model. Setting up strong security policies, automating process for efficiency, and ensuring all implementations align with the ZT implementation deadlines from Executive Order 14028, M-22-09, DoD ZT Portfolio Management Office (PfMO) Project Plan, the DoDEA ZT Implementation Plan (iPlan), and the National Institute of Standards and Technology Special Publication (NIST SP) 800-207.
Accomplishments
IBSS’ ZT Security Engineers delivered several major accomplishments, including:
- Converting Windows 11 systems (~27k) from Trellix to MDE for Antivirus and EDR.
- Assisting IT Division engineers to onboard servers into Intune, which will lead to full MDE adoption.
- Assisting Privileged Identity Management (PIM) team in establishing a secure administrator group for ZT Endpoint Administrators.
- Identifying additional gaps between Trellix and MDE capabilities such as CMRS roll-ups (SEDR) and Device Control Management.
- Collaborating with Microsoft to mitigate gaps as they were uncovered, paving the way to migrate from Trellix DLP to Microsoft’s Device Control.
Looking Forward
As new technology continues to leverage Artificial Intelligence (AI) and Machine Learning (ML), IBSS continues working with DoDEA to develop an improved security posture to better protect against zero day malware. We work with the IT Division to fill gaps, for example, maturing DoDEA’s Cybersecurity Operations Center (CSOC) to improve technical processes and analysis, as well as using innovative tools to acquire and review critical security information. As security capabilities are further automated, the IT Division will be able to adopt a truly proactive security posture with AI/ML capabilities.
The future state at DoDEA will include endpoint security protections that use MS Global Threat Intelligence to align with ZT best practices. Helping DoDEA achieve this state will lead to increased protections against zero day and file-less threats, more automated security processes, increased efficiency, and the ability to dig into more minute details by freeing staff resources to focus on more actionable threats.
IBSS will enhance and mature the existing Microsoft security stack to align with DoDEA’s ZT requirements by March 2027. Engineers are building policy leveraging Microsoft Device Control to handle all USB and removable storage management. The team is collaborating with Microsoft to enhance their baseline (STIG) scanning solution, Microsoft Defender Vulnerability Management (MDVM), to ensure it meets DoD requirements and can be utilized during audits. Efforts are underway to advance DoDEA’s host based firewall capabilities by utilizing Microsoft Defender Firewall. The IBSS engineers are working with DoDEA’s network operations team to mirror Palo Alto configurations at the endpoint level. This will ensure a device is shielded regardless of VPN connectivity. The team is also planning future MS Defender integrations with Cisco’s Identity Service’s Engine (ISE) solution to add limitless conditional access capabilities to DoDEA’s security stack.
IBSS continues to maintain a strong client relationship with DoDEA. Our ZT Endpoint Security Engineers fostered excellent working relationships over the past 6 years, which has become a major advantage for future ZT initiative planning and implementation. We similarly enjoy a strong relationship with MS, engaging on a weekly basis to identify needs and requirements for the DoDEA ZT effort. These engagements help identify critical questions and quickly remove roadblocks to maintain established timelines.
In addition, we continue developing significant crossover experience, allowing our ZT Endpoint Security Engineers to support all ZT pillars, which is unique, as there are likely limited competitors with cross functional ZT and DoD/DoDEA experience. For example, collaborations with various network SMEs allowed our ZT Endpoint Security Engineers to improve ZT capabilities for both Visibility and Analytics (VA) and Network and Environment pillars. Additionally, this crossover experience allowed IBSS to assist DoDEA in strategically reducing and/or removing on-premise infrastructure, eliminating legacy endpoint security solutions in favor of cloud solutions. As DoDEA’s legacy solution requires VPN, IBSS will assist in engineering an implementation strategy for Secure Access Service Edge (SASE) to further contribute to established ZT goals.
IBSS adds further value through understanding traditional DoD requirements (e.g., auditing, endpoint configuration, standards, and applying our experience) to find solutions that incorporate new technology to reduce non-compliance risk factors while moving DoDEA’s education mission forward. Previously, every DoD agency had licenses for software and paid for hardware, whereas now, agencies may use technology as needed, so long as it complies with established ZT guidelines. IBSS assists DoDEA in evaluating tools and technology for decommissioning due to high maintenance costs (HBSS vs. MS solution) and identifies opportunities to upgrade with cloud technology to enable future vulnerability management cost savings and a reduced physical footprint in the datacenter as a result of the decrease in hardware and license requirements.
Learn more about IBSS’ cybersecurity capabilities.
Keywords: cybersecurity, computer security company, cyber and security, security network, zero trust, endpoint security





